Recent ICMC Video Clips
Please login to get access to the full length videos.
Webinar Video Clip: Navigate Through Corporate Political Storms
Thank you to everyone who joined us for this free webinar! During the webinar, Rob Burton and David Kalson examined business challenges in political and geopolitical crises, using case studies to highlight risk management and preparedness strategies. In this short...
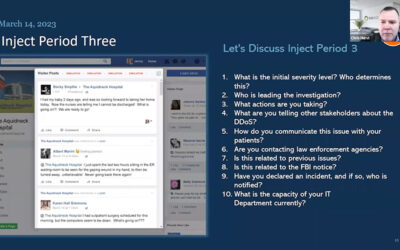
Webinar Video Clip: Northeastern Cyber Storm – A Cyber-Security Crisis Management Tabletop Exercise Walkthrough
Thank you to everyone who joined us for this free webinar! During the webinar, Rob Burton and Chris Hurst defined a cyber-attack and discussed the response to, management of, and recovery from such an attack. They walked through a cyber scenario of a fictitious...
Webinar Video Clip – Midnight Thunder: An Active Shooter Tabletop Exercise Walkthrough
Thank you to everyone who joined us for this free webinar! During the webinar, Rob Burton and Chris Britton took us on a journey through a fast-paced simulated active shooter tabletop exercise that highlighted the need for critical and timely decision-making during...
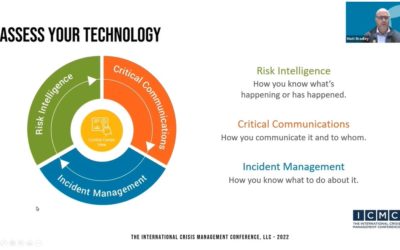
Webinar Video Clip – Pitfalls or Progress – The Challenges of Selecting Communication and Collaboration Platforms
Thank you to everyone who joined us for this free webinar! Even before the Pandemic communication and collaboration systems and platforms have become a hot topic in emergency and business resiliency circles. The use of mobile and desktop software solutions eliminates...
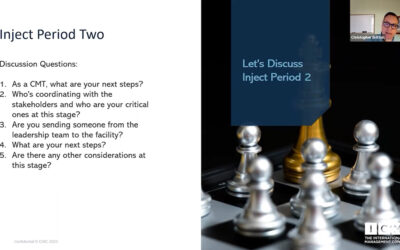
Webinar Video Clip – Crisis Response Team Activation: A Tabletop Exercise Webinar
Thank you to everyone who joined us for this free webinar! The activation of any emergency or crisis team often requires an immediate response that needs to be coordinated. In the first few moments of fast-paced situations there is often confusion and a lack of...
Webinar Video Clip – Boston Marathon Bombing Lessons for Incident Response and Business Continuity
Thank you to everyone who joined us for this free webinar! In this webinar, John Petrozzelli, Director of Cyber Security at Magna5, discussed preparation for incident response, crisis response during an incident, and post incident response through the lens of his...